I’m Being Attacked! Don’t Panic. Grab a Coffee and Relax.
In my last post I configured the OpenVPN server on an Allied Telesis AR2050V firewall.
Enabling OpenVPN means I must also have a firewall rule to allow OpenVPN traffic through the firewall. I checked out the analytics on my firewall and lo and behold—found hits against my OpenVPN firewall rule. Not just one hit but thousands. Each hit represents one attempt to open a VPN connection to my server.
Wow! My firewall log indicated I was being attacked from all around the world—some by people but most from bots trying to access my OpenVPN server. Personally, I wasn’t too worried about unauthorized people getting in, but was confused and also a little interested to understand why so many bots were persisting in their attempts to get into my firewall.
So my first step was to grab a list of attackers and create a separate firewall rule that just monitors these nuisance attempts. I called them nuisances, as they didn't get into my private network, but just pecked away at the firewall’s defenses.
Having a professional firewall allows you to dig deeper and monitor using the built-in analytics to find out what’s hitting your WAN interface. This made it easy to collect the source IP addresses of where these access attempts were coming from. From the firewall data collected over a four-day period, I observed 324,175 attempts to access my network!
Below is a partial capture of the show firewall rule output. I have only included the counters for the denied and permitted OpenVPN hits. Each hit is one attempt to access my OpenVPN server.
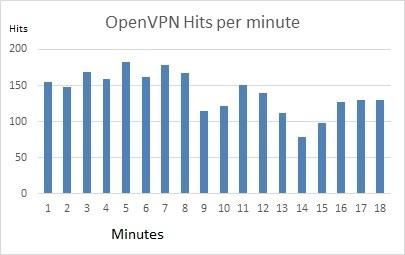
Over an 18-minute period I found that these hits were peaking at around 180 attempts per minute to brute force a successful OpenVPN tunnel session.
The bots that are trying to hack my network seem to work on brute force and high-frequency attempts against port 1194 (the port often used by OpenVPN). The bots mainly use simple linux default user id or no user id at all.
If I was just relying on a simple user id and password for protection, then I’d be worried right now. But my AR2050V firewall uses an x509 certificate with more than 1024-bit encryption, so the chances of breaking in are worse than winning the USA Powerball lottery!
Until someone successfully breaks in, I’ll enjoy the peace of mind my AR2050V firewall gives me—and the sound sleep I have every night!