Registering Actions
What is Action
AT-SESC has an authentication rule called Action. In addition to processing by device authentication data and the UnAuth Group, this device individually isolates or blocks devices that meet specific conditions, or connects to a network different from the device authentication data registration.If you are using external security applications which are interacting with AT-SESC, actions are automatically generated and executed when AT-SESC receives instructions from those applications.
You can also manually create actions without using external applications.
In either case, the Action takes precedence over the Device Authentication Data and the UnAuth Group.
You can use the following data as conditions for an action.
- Device MAC Address
- Device IPv4 Address
- Device
- Device Tag
- Location
- OpenFlow Switch
- Connecting Network
Actions with the conditions including Device MAC Address, Device IPv4 Address, Device or Device Tag are also used by the AMF Application Proxy.
- When a Device MAC Address is specified → The MAC address is sent to the AMF Master
- When a Device IPv4 Address is specified → The IPv4 address is sent to the AMF Master
- When a Device MAC Address and a Device IPv4 Address are specified → Only the IPv4 Address is sent to the AMF Master
- When a Device or a Device Tag is specified → The MAC address associated with the device is sent to the AMF Master
Manually Adding Action
Action can be registered on the Policy Settings > Add Action page.
A suspicious packet was sent from the device with MAC address "00:00:5E:00:53:01" connected to the OpenFlow Switch "AT-TQ4400" that provides the guest network to the UnAuth Group. The following explains how to block the communication of this device. To add an action manually, follow those steps:
- Open the Policy Settings > Action List page.
This page shows the list of actions. As you see, no action is registered at this point.
- Click the "Add Action" button at the top right corner of the Policy Settings > Action List page to open Policy Settings > Add Action page.
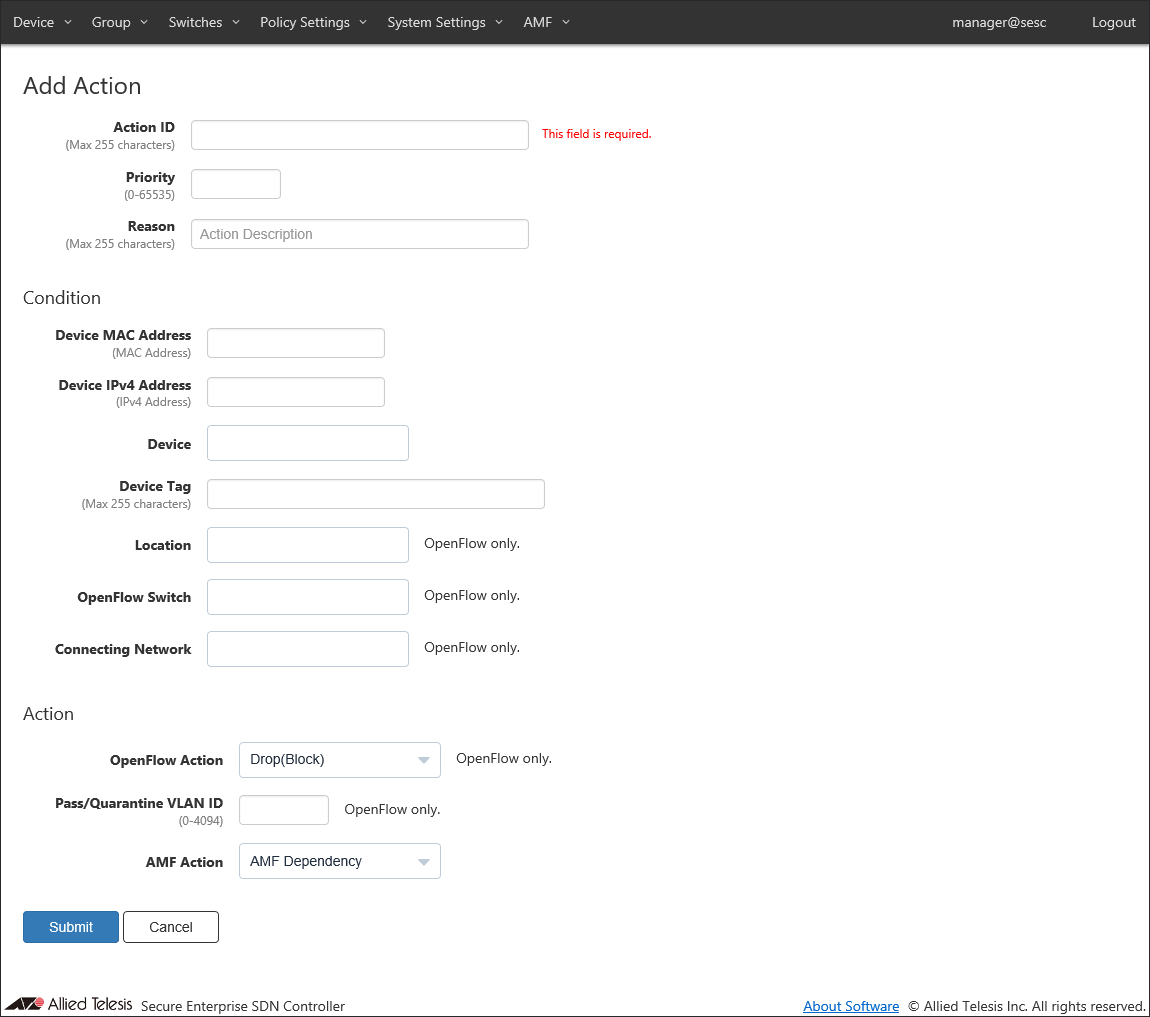
- Enter information for the action to add.
As an example, configure the settings shown in the following table: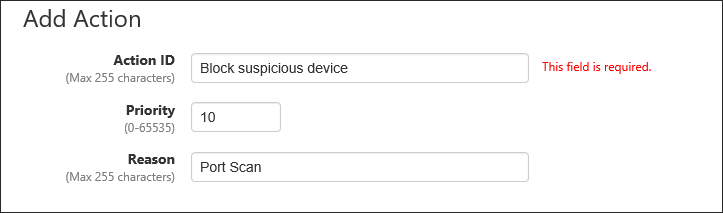
Table 1: Sample Configuration Data
Item Name Value Description Action ID (Mandatory) Block suspicious device ID (Name) of the action.
Action ID must be unique.
Max 255 charactersPriority 10 Priority of the action. It must be an integer between 1 and 65535.
Smaller number has higher priority. Thus the matching action with the smaller priority value is executed.
Priority value is set to 10 if it is unspecified.Reason Port Scan Administrative comment such as a reason for running this action.
Max 255 characters
- Enter conditions to trigger the action.
In this example, specify the suspicious device as Device MAC Address.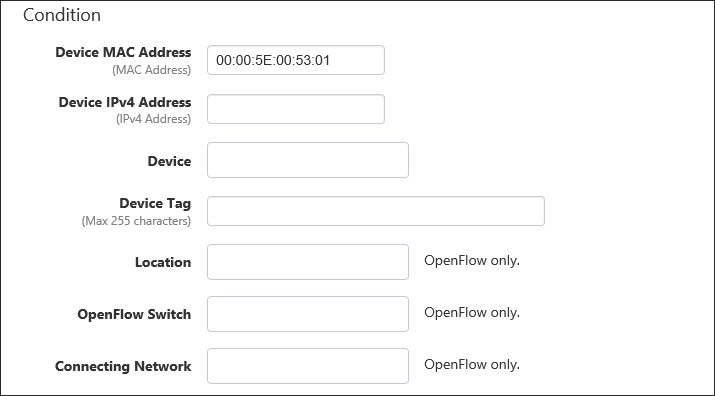
Table 2: Sample Configuration Data / Conditions
Item Name Value Description Device MAC Address 00:00:5E:00:53:01 Unicast MAC address of the target device.
Valid formats are as follows
xx:xx:xx:xx:xx:xx, xx-xx-xx-xx-xx-xx, xxxx.xxxx.xxxxDevice IPv4 Address (empty) Unicast IPv4 address of the target device. Device (empty) Device ID of the target device.
Maximum 100 device IDs are shown in the dropdown list. If you enter text in the field, device IDs in the dropdown list are dynamically filtered to the ones which contain the input text in Device ID, Tag or Note (it shows maximum 100 elements). From the dropdown list, select a Device ID for the device.Device Tag (empty) Device Tag of the target device. Location (empty) Location ID for the target device.
Maximum 100 IDs of the existing locations are shown in the dropdown list. If you enter text in the field, location IDs in the dropdown list are dynamically filtered to the ones which contain the input text in Location ID or Note (it shows maximum 100 elements). From the dropdown list, select a Location ID.OpenFlow Switch (empty) Switch ID for the target device.
Maximum 100 IDs of the existing switches are shown in the dropdown list. If you enter text in the field, switch IDs in the dropdown list are dynamically filtered to the ones which contain the input text in Switch ID, Datapath ID, Upstream Port or Note (it shows maximum 100 elements). From the dropdown list, select a Switch ID.Connecting Network (empty) Network ID for the target device.
Maximum 100 IDs of the existing networks are shown in the dropdown list. If you enter text in the field, Network IDs in the dropdown list are dynamically filtered to the ones which contain the input text in Network ID, VLAN ID or Note (it shows maximum 100 elements). From the dropdown list, select a Network ID.
- Enter the action to perform when a device met the conditions.
In this example, the communication from the device is discarded, so it is not necessary to specify the Pass/Quarantine VLAN ID.
Also, leave the AMF Action as default ("AMF Dependency") because the AMF Application Proxy is not used in this example.
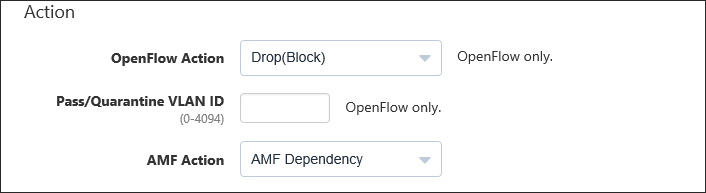
Table 3: Sample Configuration Data / Action
Item Name Value Description OpenFlow Action Drop(Block) OpenFlow action to run on the target device. - Pass(Permit): Permit traffic from the device.
- Quarantine: Move the device to the quarantine network.
- Drop(Block): Block traffic from the device.
- Log-Only: AT-SESC does not specify an action and records the device information.
Pass/Quarantine VLAN ID (empty) A VLAN ID on which the device is allowed to transmit packets. AMF Action AMF Dependency An action to be taken on the AMF network deploying AMF Application Proxy feature. - AMF Dependency: AT-SESC does not specify an action and lets AMF devices determine its action.
- Quarantine: Move the port where the device is connected to the quarantine VLAN.
- Drop Packets: Block traffic from the device at the layer two (MAC) level.
- Link-Down: Shutdown the port where the device is connected.
- IP-Filter: Block traffic from the device at the layer 3 (IP) level.
- Log-Only: Record the device information.
Note
To use the AMF Action "Log-Only", your Proxy Node and Edge Nodes must have AlliedWare Plus firmware version 5.4.9-0.x or later installed.
- Click "Submit".
Once the action was added, the Policy Settings > Action List page reflects the added information.
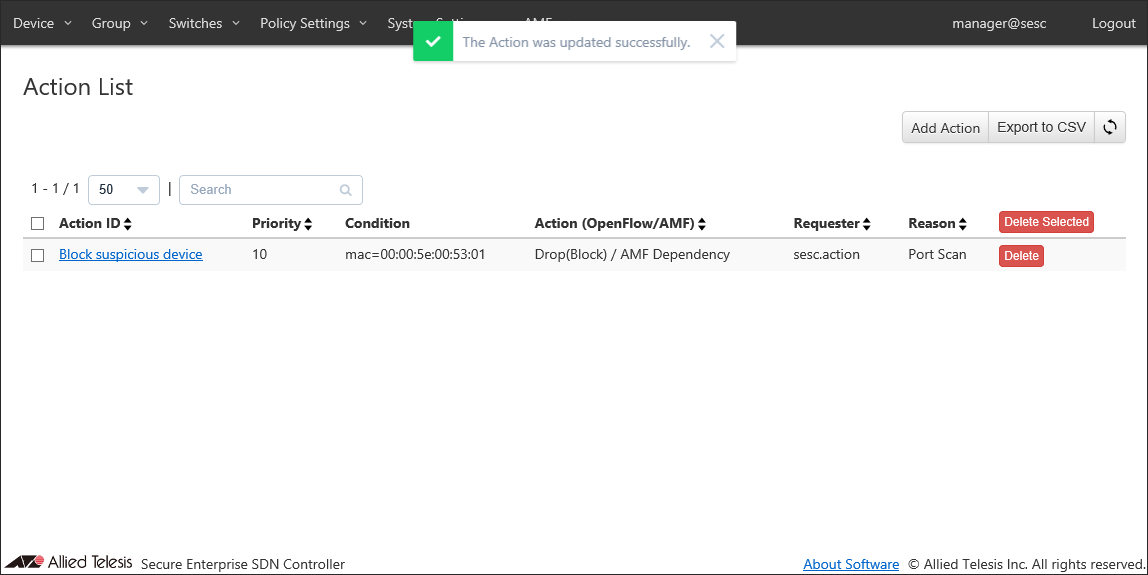
After the action is activated, all traffic from the MAC address is dropped unless you delete the action or you add an action with higher priority (smaller priority value) to permit the MAC address.
14 Jun 2021 09:30