AMF
AMF Application Proxy Settings
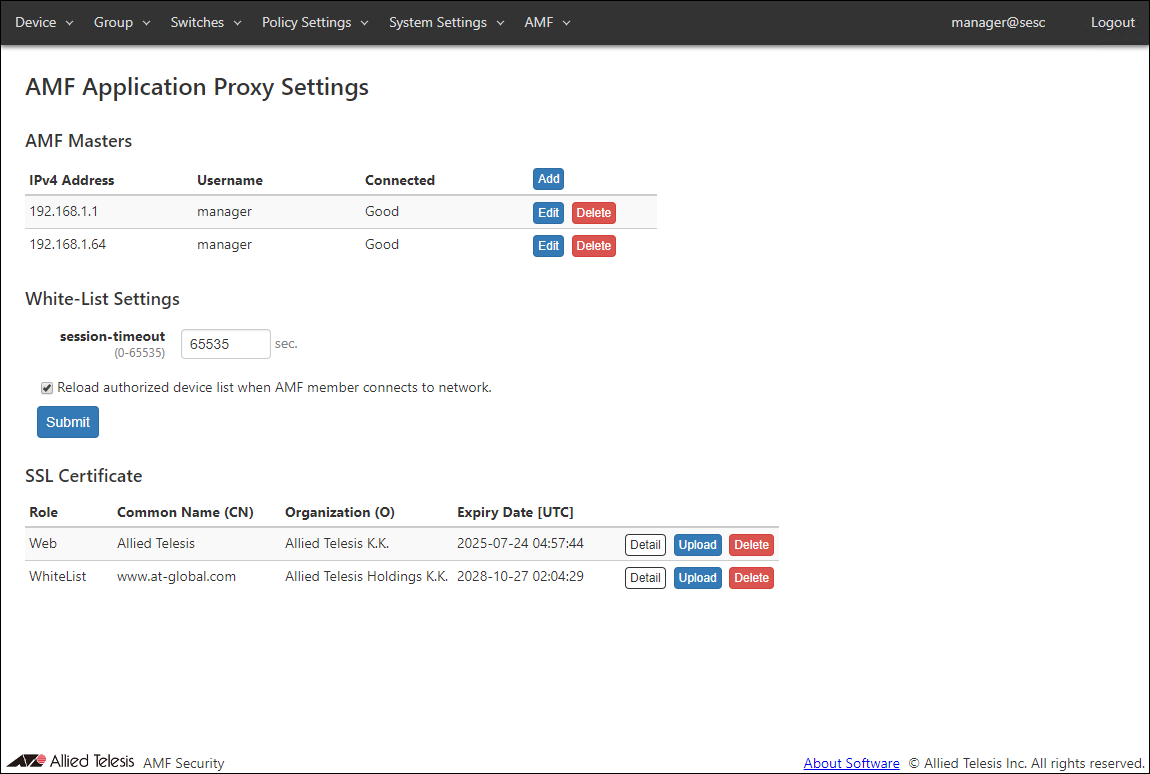
AMF Masters
Register the AMF Master in AMF Security. It also shows a list of registered AMF Masters.NoteWith the following settings, the connection with connected OpenFlow Switch or AMF Master is temporarily disconnected.
・AMF Master
・White-List Settings
・Uploading or deleting the SSL Certificate of the Web server
| Item Name | Description |
|---|---|
| IPv4 Address | IPv4 address of AMF Master using AMF Application Proxy. |
| Username | Username of a level 15 (privileged) account on the AMF Master. |
| Connected | Displays the connection status with the AMF Master, Good, Error, Checking, or Disconnected. Disconnected is displayed when the base license is not registered. |
| Item Name | Description |
|---|---|
| Add | Open Edit AMF Master dialog to register a new AMF Master. |
| Edit | Open the Edit AMF Master dialog to update AMF Master information. |
| Delete | Delete information of the selected AMF Master. |
Edit AMF Master
This dialog lets you add or edit information of AMF Master.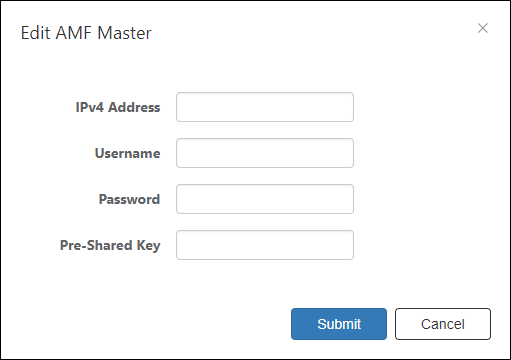
| Item Name | Description |
|---|---|
| IPv4 Address | Enter an IPv4 address of AMF Master using AMF Application Proxy. Then enter the username and password below. |
| Username | Enter a username of a level 15 (privileged) account on the AMF Master. |
| Password | Enter a password for the above username. |
| Pre-Shared Key | Enter a pre-shared key used between the AMF Master and the Whitelist Server (AMF Security). |
NoteThe same privilege level 15 (privilege level) account must be set up for all AMF Members.
| Item Name | Description |
|---|---|
| Bottom of the dialog | |
| Submit | Register a new AMF Master or update information of an existing AMF Master. |
| Cancel | Cancel the operation for registering or updating AMF Master information. |
NoteWhen you finish this configuration, the AMF Master (proxy node) is contacted periodically (every 30 seconds) in order to acquire edge node information.
It is recommended that the AMF Master account (Username and Password) set for AMF Security be different from the user account used for AMF Member console connection. Create a user account with authority level 15 in advance by AMF Master and AMF Member.
When sharing the user account used for the console connection of AMF Master and AMF Member with the account set in AMF Security, set the lockout time for login failure of AMF Master and AMF Member to less than 5 minutes (use "aaa local authentication attempts lockout-time" command). Please note that the user is not able to log in under the following conditions and operations. - Lockout time for AMF Master and AMF Members when login fails is set to 5 minutes or more - Share the AMF Master and AMF Member CLI connection account with the account set in AMF Security. If the above two conditions are met and the account is locked out due to consecutive failures to log in to the AMF Master and AMF Members, or if the AMF Master account setting is incorrect in AMF Security, The node information of the AMF network cannot be obtained from AMF Security, and the lockout timer is continuously updated by polling from AMF Security, so that the user cannot log in.
White-List Settings
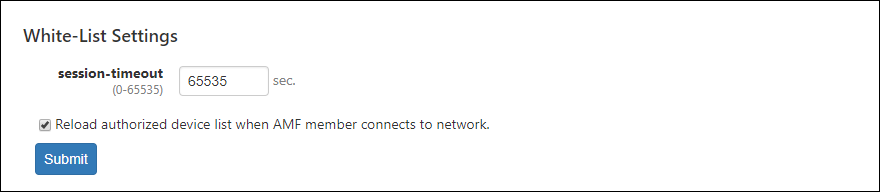
| Item Name | Description |
|---|---|
| session-timeout | Specify a timer value (in seconds) to be configured on the switch when a device is successfully authenticated. When the timer expires, the device is reset to unauthenticated state. Valid range is 0 to 65535. Default is 65535. When set to zero, nodes are always in authenticated state because no timer is configured on switches. This value is used when a security policy for a device does not have Schedule. This value may be preceded by a Schedule's End Date / Time. This value is used as it is when the interval between the successful authentication and a scheduled End Date / Time is less than 65535 seconds. If the interval between the successful authentication and a scheduled End Date / Time is larger than or equals to 65535 seconds, actual timeout is set to 65535 seconds. |
| Reload authorized device list when AMF member connects to network. | The node information authenticated by the AMF Application Proxy displayed on the Device > Active Device List page is reloaded when AMF Security is restarted. To use this feature, your Proxy Node and Edge Nodes must have AlliedWare Plus firmware version 5.4.9-1.x or later installed. Also, enable the "service http" command on both the Proxy Node and the Edge Nodes. |
| Item Name | Description |
|---|---|
| Submit | Save the settings. |
SSL Certificate
Register the SSL server certificate of the Web server (AMF Security) and the SSL server certificate of the whitelist authentication server installed in AMF Security.If you want external applications to interact with AMF Security via HTTPS, you may have to install an SSL server certificate issued by a trusted certificate authority (CA).
If you want to encrypt control session between AMF Master and Whitelist Server (AMF Security), upload an SSL server certificate issued by a trusted certificate authority (CA).
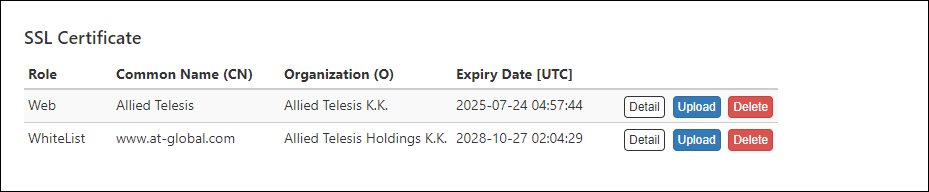
"SSL Certificate" section shows a summary of the installed SSL server certificate.
- If your CA provides you with intermediate CA certificates or cross root CA certificates in addition to your server certificate, concatenate those certificates into a single file then upload the file to AMF Security. Contact the CA for detailed information on how to concatenate certificate files.
- To install a certificate file, it must meet the following requirements.
Table 7: SSL Certificate Requirements
Type X.509, RFC6818 Encryption PEM (Privacy Enhanced Mail) Extension .crt
| Item Name | Description |
|---|---|
| Role | Displays Web (Web server) or WhiteList (Authentication server). |
| Common Name(CN) | Displays the common name of the web server (AMF Security) or authentication server (AMF Security). |
| Organization(O) | Displays the name of the organization to which the Web server (AMF Security) or authentication server (AMF Security) belongs. |
| Expiration Date [UTC] | Expiration date of the certificate. |
| Item Name | Description |
|---|---|
| Detail | The detailed information of the registered SSL server certificate is displayed. |
| Upload | Open the Upload SSL Certificate dialog to register the SSL Certificate with AMF Security. |
| Delete | Delete the installed SSL server certificate and restore the default certificate which is self-signed by AMF Security. |
NoteAfter setting the AMF master, AMF Security accepts both unencrypted and encrypted sessions. You cannot disable one of them.
Upload SSL Certificate
This dialog lets you upload your own SSL Certificate for the White-list Authentication Server.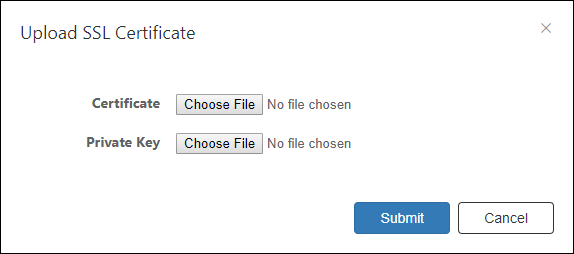
| Item Name | Description |
|---|---|
| Certificate | Click the "Choose File" button and select the SSL Certificate to upload. |
| Private Key | Click the "Choose File" button and select the SSL private key to upload. |
| Item Name | Description |
|---|---|
| Submit | Import the specified private key and certificate. |
| Cancel | Cancel the operation for importing SSL Certificate. |
TQ Settings (not supported)
NoteDo not register this page as it is not supported.
14 Jun 2021 09:30