Configuring AT-AR3050S/AT-AR4050S
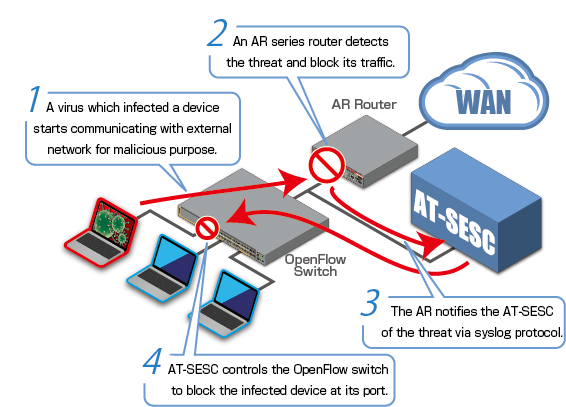
Advanced VPN Access Router AT-AR3050S/AT-AR4050S series (AR Router) is the next generation firewall router with the rich set of security features such as firewall, IPS/IDS, anti-virus, malware-protection and IP reputation in addition to the VPN router functions. AT-SESC can use the threat information provided by the AR Router to control the OpenFlow Switches so that it can dynamically manage and operate client devices connected to the switches.
Supported UTM Features
AT-SESC can use the threat information detected by the AR Router's following UTM functions.NoteAT-SESC can utilize the UTM features with UTM offload enabled.
◼ IP Reputation
Using the IP reputation database, it controls packets from or to the specific IP address. AT-SESC can use the following categories.
| Category | Category Name (NAME parameter) |
Description |
|---|---|---|
| Malware | CnC Malware C&C Server |
C&C Server which sends command to the known malware (bot). This category contains the domains and IPs which are observed and DGA predicted. |
| Bot Malware-infected Host |
A host observed checking in to a command and control server, or exhibiting clear indications of unwanted and criminal code on the host. | |
| Mobile_CnC Mobile C&C Server |
Known CnC for Mobile specific Family | |
| Spyware | Drop Leaked Information Site |
Drop site for logs or stolen credentials. Differentiated from CnC servers, but sometimes overlapping. Does not include droppers being served or other exe movement. |
| SpywareCnC Spyware C&C Server |
Servers and domains observed being used to serve or track user activity. It is more likely to be a destination for information collected by software such as toolbars, games, and free screen savers, rather than regular ad serving sites. | |
| Mobile_Spyware_CnC Mobile Spyware C&C Server |
Spyware CnC specific to mobile devices |
NoteTo use this feature, license is required for AR Router.
◼ Firewall
AR Router has the stateful inspection firewall which identifies the start and end of the IP traffic flows and perform dynamic packet filtering on the flow information. AT-SESC can handle the information about the following attacks detected by AR Router in addition to the Firewall events.
| Attack | Description |
|---|---|
| Syn Flood | Detected when the number of TCP SYN packets in a second from the specific IPv4 address reaches the threshold. |
| ICMP Flood | Detected when the number of ICMP packets in a second from the specific IPv4 address reaches the threshold. |
| UDP Flood | Detected when the number of UDP packets in a second from the specific IPv4 address reaches the threshold. |
| TCP Stealth Scan | Detected when an invalid TCP packets (IPv4 only). |
◼ Malware Protection
AR Router can inspect data in the application-layer of the packets going through the router and block or notify when the known malware is detected.
All the threat detected by this feature can be used by AT-SESC.
NoteTo use this feature, license is required for AR Router.
◼ Antivirus
AR Router can scan the file included in HTTP responses going through the router and block or notify when the known virus is detected.
All the threat detected by this feature can be used by AT-SESC.
NoteTo use this feature, license is required for AR Router.
NoteAntivirus is supported on AT-AR4050S only.
Configuring AR Router
Please refer to the AR Router's documentation for its configurations.AR Router manuals are available on our website.
14 Jun 2021 09:30